
Apple Addresses Critical Security Flaw in Apple iOS 18.3.1 and iPadOS 18.3.1 Updates: A Deep Dive into the USB Restricted Mode Vulnerability
In an era where digital security is paramount, Apple has once again demonstrated its commitment to safeguarding user data with the release of its Apple iOS 18.3.1 and iPadOS 18.3.1 updates. These patches, rolled out on February 11, 2025, come just two weeks after the company’s previous major updates (Apple iOS 18.3 and iPadOS 18.3) and focus exclusively on resolving a critical security vulnerability rather than introducing new features. This article delves into the specifics of the exploit, its implications, and the broader context of Apple’s USB Restricted Mode—a security feature now at the heart of this urgent update.
The Vulnerability: Exploiting Accessibility Services to Bypass USB Restricted Mode
The centerpiece of this update is a fix for a flaw within Apple’s Accessibility services, which malicious actors could exploit to disable the USB Restricted Mode on locked iPhones and iPads. According to Apple’s release notes, the vulnerability allowed attackers with physical access to a device to circumvent this critical security layer, potentially granting them unfettered access to sensitive user data stored on the device.
How the Exploit Works
In a physical attack scenario, an attacker could manipulate the Accessibility service—a suite of tools designed to assist users with disabilities—to turn off USB Restricted Mode even while the device remained locked. Once disabled, the attacker could connect the iPhone or iPad to specialized hardware or software (such as law enforcement tools like GrayKey) to extract personal information, including messages, photos, and encryption keys. Apple confirmed that this vulnerability was exploited in “an extremely sophisticated attack targeting specific individuals,” though details about the victims or perpetrators remain undisclosed.
The Critical Role of Physical Access
A key detail in this exploit is the requirement for physical access to the device. Unlike remote hacking attempts, which can target millions of users indiscriminately, this vulnerability hinges on an attacker having direct, hands-on contact with the iPhone or iPad. This specificity suggests that the risk is highest for high-profile individuals—such as journalists, activists, or executives—whose devices might be deliberately stolen or seized. For the average user, the likelihood of such a targeted attack is low, though the update remains essential for all eligible devices.
USB Restricted Mode: A Primer on Apple’s Defense Against Unauthorized Access
To fully grasp the significance of this patch, it’s crucial to understand the role of USB Restricted Mode, a security feature introduced in 2018 with Apple iOS 11.4.1.
What Is USB Restricted Mode?
USB Restricted Mode is designed to block unauthorized USB accessories from communicating with a locked device after it has been inactive for one hour. This measure thwarts brute-force attacks and data extraction tools that rely on prolonged access via the Lightning or USB-C port. As Apple explains on its support page, “If you haven’t unlocked your device or connected it to a trusted accessory within the past hour, your device won’t communicate with new accessories or computers—and in some cases, might not even charge.”
Why Was It Created?
The feature emerged in response to growing concerns about tools like GrayKey, a device used by law enforcement and hackers to bypass iPhone encryption. By limiting USB access after a set period, Apple aimed to protect users—particularly those at risk of device confiscation—from having their data extracted without consent. This update underscores the ongoing cat-and-mouse game between tech companies and entities seeking to circumvent security measures.
The Exploit’s Implications: Security vs. Sophistication
While Apple has not disclosed technical specifics of the exploit (to prevent further misuse), the incident highlights several critical themes in modern cybersecurity:
- The Value of Physical Security
No matter how robust a device’s encryption, physical access remains a potent attack vector. This exploit serves as a reminder to users to safeguard their devices against theft or unauthorized handling. Features like Find My iPhone and strong passcodes (preferably alphanumeric) are vital first lines of defense. - The Targeting of High-Risk Individuals
Apple’s acknowledgment of “specific targeted individuals” aligns with a broader trend of advanced persistent threats (APTs) focusing on high-value targets. Such attacks often involve meticulous planning, custom tools, and social engineering, making them difficult to detect and counter. - Apple’s Responsiveness to Threats
The swift release of this patch—15 days after the prior update—reflects Apple’s ability to rapidly address critical vulnerabilities. This agility is central to maintaining user trust, especially as cyber threats grow more sophisticated.

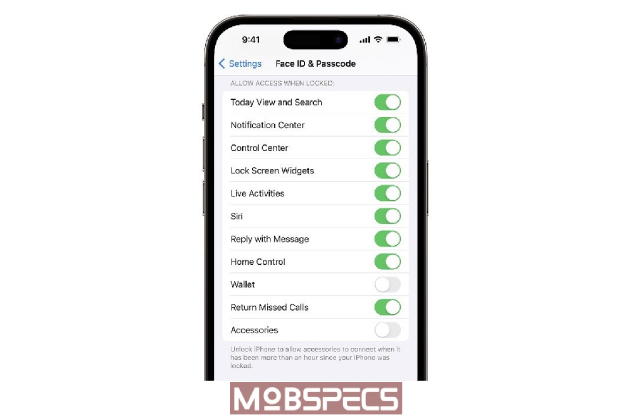
How to Check if USB Restricted Mode Is Enabled
Given the exploit’s focus on USB Restricted Mode, users should verify that this feature is active on their devices. Here’s a step-by-step guide:
- Open the Settings App: Navigate to the iOS or iPadOS home screen and launch Settings.
- Access Face ID & Passcode Settings: Scroll to “Face ID & Passcode” (or “Touch ID & Passcode” on older devices).
- Authenticate: Enter your device passcode when prompted.
- Review ‘Allow Access When Locked’: Scroll to this section and ensure the “Accessories” toggle is off. If disabled, USB Restricted Mode is active, blocking unauthorized accessories after one hour of inactivity.
Pro Tip: For added security, enable “Erase Data” in the same menu, which wipes the device after ten failed passcode attempts—a deterrent against brute-force attacks.
Broader Context: Apple’s Security Philosophy and User Responsibility
This incident underscores Apple’s longstanding emphasis on privacy and security, pillars that differentiate its products in a crowded market. However, it also highlights the shared responsibility between companies and users. While Apple works to patch vulnerabilities, users must:
- Install Updates Promptly: Delaying iOS updates leaves devices exposed to known exploits.
- Use Strong Authentication: Complex passcodes and biometrics (Face ID/Touch ID) add critical layers of protection.
- Avoid Untrusted Accessories: Malicious chargers or cables can exploit USB vulnerabilities.
Historically, Apple has faced criticism over security flaws, such as the 2017 “GrayKey” revelations or the 2020 “Pegasus” spyware scandal. Yet its consistent response—rapid patches, transparency reports, and hardware-level security innovations like the Secure Enclave—demonstrates a proactive approach to mitigating risks.
Conclusion: A Call to Action for Users
The Apple iOS 18.3.1 and iPadOS 18.3.1 updates may lack flashy new features, but their importance cannot be overstated. By patching a vulnerability that undermines USB Restricted Mode, Apple has closed a door that could have led to significant data breaches for targeted users.
For most individuals, the update is a routine safeguard. For those in high-risk categories, it’s a critical line of defense. As cyber threats evolve, so too must our vigilance. Ensuring devices are updated, practicing physical security, and leveraging Apple’s built-in protections remain the best strategies for staying ahead of adversaries. In the words of Apple’s security team, “Security is a journey, not a destination”—and this update is a pivotal step on that journey.
Final Recommendation: All eligible iPhone and iPad users should install Apple iOS 18.3.1/iPadOS 18.3.1 immediately via Settings > General > Software Update. In an interconnected world, staying secure is not just an option—it’s a necessity.
Also Read Below:
How Apple success is pushing Qualcomm and MediaTek to innovate in 2025
iPhone SE 4 Release Date and Features: What to Expect from Apple’s Affordable Powerhouse